Your SPF record is the go-to resource for recipients’ mailboxes to check if a certain sender’s IP address or mail server is allowed to transmit emails on behalf of your company. You’ll come across SPF neutral, Softfail, or Hardfail error if any of the following is true in your SPF TXT record:
- Unable to resolve to the domain name in DNS.
- A non-existing SPF record.
- Presence of multiple SPF records.
- Syntax errors.
- Missing IP addresses or mail servers.
- Exceeding the maximum limit of 10 DNS lookups.
- Exceeding the maximum limit of 2 void lookups.
Getting rid of these issues helps with proper DKIM, DMARC, and SPF authentication drills.
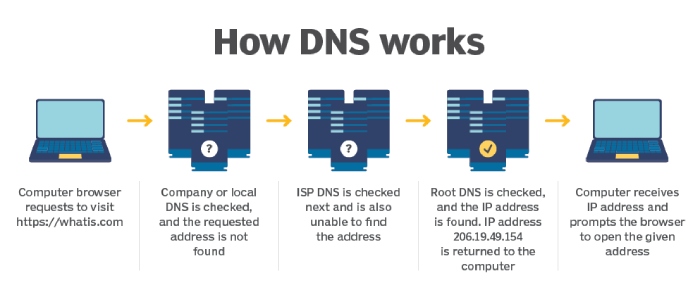
Image sourced from techtarget.com
SPF Neutral
SPF neutral is an error represented by the ?all tag and occurs when SPF records for the senders’ domains don’t explicitly indicate whether servers or IP addresses in question are authorized. This issue can pop up due to a misconfigured or missing SPF record for your organization’s official email-sending domain.
SPF neutral errors can sometimes occur due to legitimate reasons such as complex email forwarding setups. However, they can also be exploited by spammers or attackers to send fraudulent emails that appear more legitimate than they are. It’s important to properly configure SPF records to minimize SPF neutral problems for enhanced email deliverability and security.

SPF Softfail
SPF Softfail is indicated by ~all tag. This error occurs when an email server or IP address isn’t part of the published SPF DNS record, but SPF policy still allows the email through with a designated “softfail” result. This implies a weaker verification level compared to a “fail” result. In this case, the message is marked as suspicious and gets placed in the spam folder. It’s recommended for domain owners to set their records to Softfail so that email messages that are wrongly concluded as fraudulent can still show up in the desired mailboxes, even if they land in the spam folders and not the primary inboxes.
This provides a degree of flexibility, allowing legitimate emails from servers not explicitly listed to be still delivered while adding a layer of caution to potential phishing attempts or unauthorized usage.
SPF Hardfail
SPF Hardfail is represented by -all tag. This SPF problem occurs when the sending mail server is not listed in the domain’s SPF record, and the receiving server should consider the email suspicious or potentially fraudulent. In this case, emails bounce back.
When to Use SPF Hardfail?
Use SPF Hardfail when you want strict control over which servers can send emails on your domain’s behalf. This ensures that unauthorized servers’ emails are outright rejected, minimizing the risk of spoofing and phishing.
When Not to Use SPF Hardfail?
Here are the typically recommended uses cases for SPF Hardfail:
- Complex Email Infrastructure: If your domain has a complex email setup involving third-party services or forwarding, a hardfail might lead to false positives, causing legitimate emails to be rejected.
- Gradual Deployment: If you’re implementing SPF for the first time, starting with a softer policy like “softfail” might be prudent. This allows you to gradually assess the impact on legitimate email flows before enforcing a strict hardfail policy.
- Compatibility Concerns: Some older email servers might not fully support SPF or interpret hardfail correctly, potentially causing delivery issues.

Summary
SPF issues like neutral, softfail, or hardfail arise from problems in the SPF TXT record: domain name resolution failure, non-existent record, multiple records, syntax errors, missing IPs, exceeding 10 DNS lookups, or 2 void lookups. Addressing these issues aids DKIM, DMARC, and SPF authentication. SPF neutral (?all) occurs from misconfigured or missing SPF records, sometimes enabling spammers. SPF softfail (~all) lets suspicious emails into spam folders while allowing flexibility for legitimate ones. SPF hardfail (-all) rejects unauthorized emails, but consider complexities, deployment stages, and compatibility.